Codeql在windows上配置及使用
参考文章:https://blog.51cto.com/u_14149124/5707132
配置
下载引擎: https://github.com/github/codeql-cli-binaries/releases/latest/download/codeql.zip
解压缩后设置环境变量
下载SDK(直接解压缩后使用):https://github.com/github/codeql
解压后使用
vscode-查看-扩展-在应用商店中搜索-codeql
vscode-设置-搜索codeql-Code QL › Cli: Executable Path-
设置为引擎的路径
C:\Users\tea90\Documents\tea\tools\codeql\codeql\codeql\codeql.exe
使用
建立数据库
codeql database create codeqltest –language=python
会生成一个codeqltest目录
vscode-codeql标签-DATABASES-添加文件夹把生成的codeqltest数据库添加
Java
参考:https://www.yuque.com/loulan-b47wt/rc30f7/xyf880
因为java是需要环境编译的不能直接用python那种直接生成数据库
参考大佬的文章可以下载WebGoat 然后就可以生成数据库了
1
2
3
4
5
6
7
8
9
| git clone --branch v8.0.0 https://github.com/WebGoat/WebGoat.git
我在这个问题卡了很久,
errno 10054 fatal: error reading section header ‘shallow-info’
git config --global http.sslVerify "false"
fatal: unable to access ‘xxxx’: OpenSSL SSL_read: Connection was
reset, errno 10054
要关代理 然后重启命令行才可以
最后不知道试了好几次才下下来
|
下载完WebGoat之后进入目录 生成数据库
1
2
3
4
| codeql database create webgoat-aldb -l java
...
90\Documents\tea\tools\codeql\codeql\codeql\xml\tools\index-files.cmd, C:\Users\tea90\Documents\tea\tools\codeql\WebGoat\webgoat-qldb\working\files-to-index4656643679450222038.list]
Successfully created database at C:\Users\tea90\Documents\tea\tools\codeql\WebGoat\webgoat-qldb.
|
生成成功
编写.ql文件之后右键选择CodeQL:Run Query on Selected Database 之后有结果右侧会出现
以下为大佬写的webgoat sql注入例子
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| webgoat-query.ql
import java
import semmle.code.java.dataflow.DataFlow
import semmle.code.java.dataflow.FlowSources
import semmle.code.java.dataflow.TaintTracking
class MyTaintTrackingConfiguration extends TaintTracking::Configuration {
MyTaintTrackingConfiguration() {
this = "MyTaintTrackingConfiguration"
}
override predicate isSource(DataFlow::Node source) {
exists(source.asParameter())
}
override predicate isSink(DataFlow::Node sink) {
exists(Call call |
sink.asExpr() = call.getArgument(0) and
call.getCallee().hasQualifiedName("java.sql", "Statement", "executeQuery")
)
}
}
from DataFlow::Node source, DataFlow::Node sink, TaintTracking::Configuration config
where config.hasFlow(source, sink)
select source, sink
|
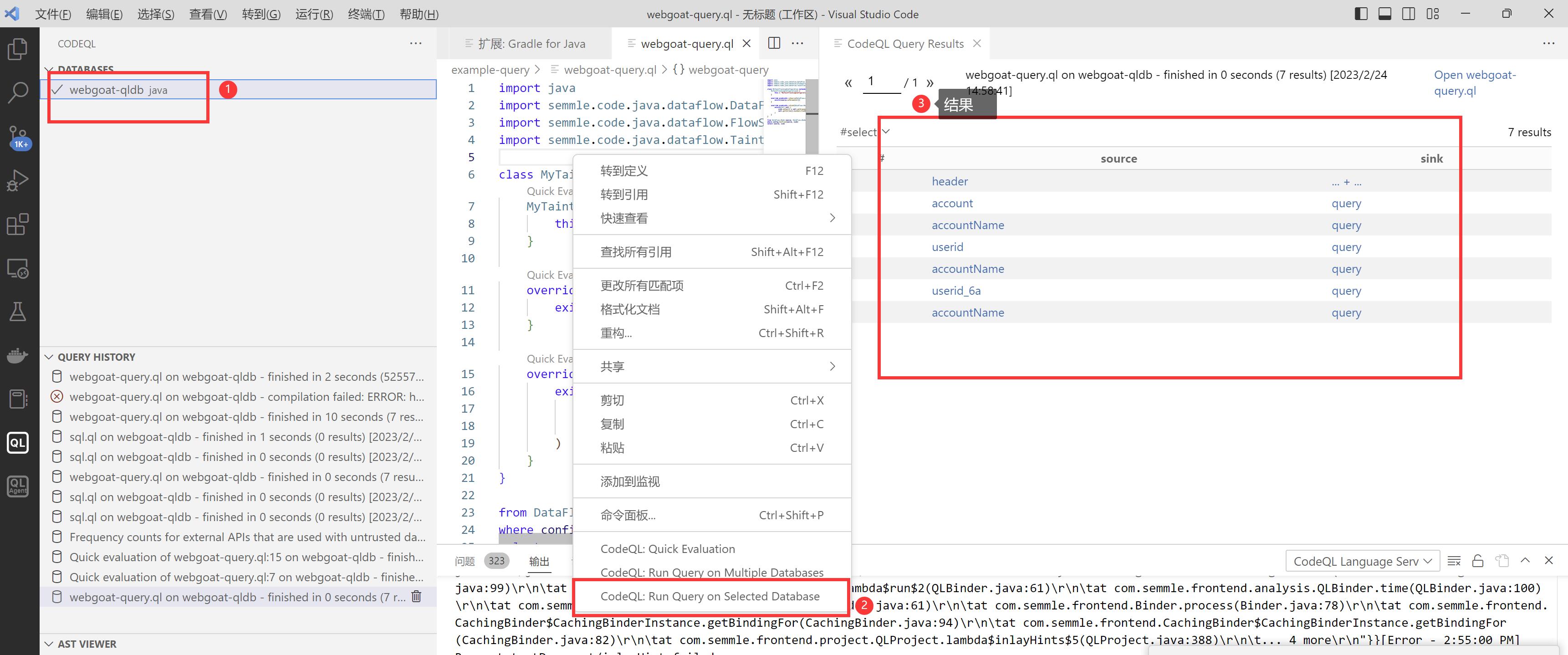
可以看到右侧搜索到的结果
白盒扫描时执行所有ql
进入到生成codeql数据库目录 没运行成功不知道哪里没有配置对
codeql database analyze source_database_name C:\Users\tea90\Documents\tea\tools\codeql\ql\ql\ql\src\codeql-suites\ql-code-scanning.qls –format=csv –output=java-results.csv
java ql常见规则
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
| java
1、zip slip(zip解压覆盖任意文件)
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-022/ZipSlip.ql
2、命令注入
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-078/ExecUnescaped.ql
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-078/ExecTainted.ql
3、cookie安全
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-312/CleartextStorageCookie.ql
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-614/InsecureCookie.ql
4、XSS
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-079/XSS.ql
5、依赖漏洞
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-1104/MavenPomDependsOnBintray.ql
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-829/InsecureDependencyResolution.ql
6、反序列化
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-502/UnsafeDeserialization.ql
7、http头注入
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-113/NettyResponseSplitting.ql
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-113/ResponseSplitting.ql
8、url跳转
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-601/UrlRedirect.ql
9、ldap注入
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-090/LdapInjection.ql
10、sql注入
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-089/SqlTainted.ql
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-089/SqlUnescaped.ql
11、file权限&目录注入
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-732/ReadingFromWorldWritableFile.ql
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-022/TaintedPath.ql
12、xml注入
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-611/XXE.ql
13、SSL校验
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-297/UnsafeHostnameVerification.ql
14、弱加密
https://github.com/github/codeql/java/ql/src/Security/CWE/CWE-327/BrokenCryptoAlgorithm.ql
15、随机数种子可预测
https://github.com/github/codeql/blob/main/java/ql/src/Security/CWE/CWE-335/PredictableSeed.ql
|
Author:
tea9
Permalink:
http://tea9.xyz/post/3359759625.html
License:
Copyright (c) 2017-2023 CC-BY-NC-4.0 LICENSE
Slogan:
Do you believe in DESTINY?
