0x00 准备 下载链接:
手机设备:
google pixel xl(android 8) 已经root
需要安装drozer-agent
windows:
需要安装drozer服务端 推荐使用docker安装
1 docker pull fsecurelabs/drozer
需要安装jadx-gui
还需要安装adb
安装:
1 adb install InjuredAndroid-1.0.12-release.apk
打开:
Challenge 0 XSSTEST browse the displaypostxss activity to see what makes this activity vulnerable
fun no flag vulneravle xss field to test payloads
浏览displaypostxss活动,查看是什么使该activity易受攻击
发现没有flag漏洞测试有效载荷的xss字段
第0个根据提示需要看代码找到xss的Activity,然后没有flag
用jadx-gui打开apk
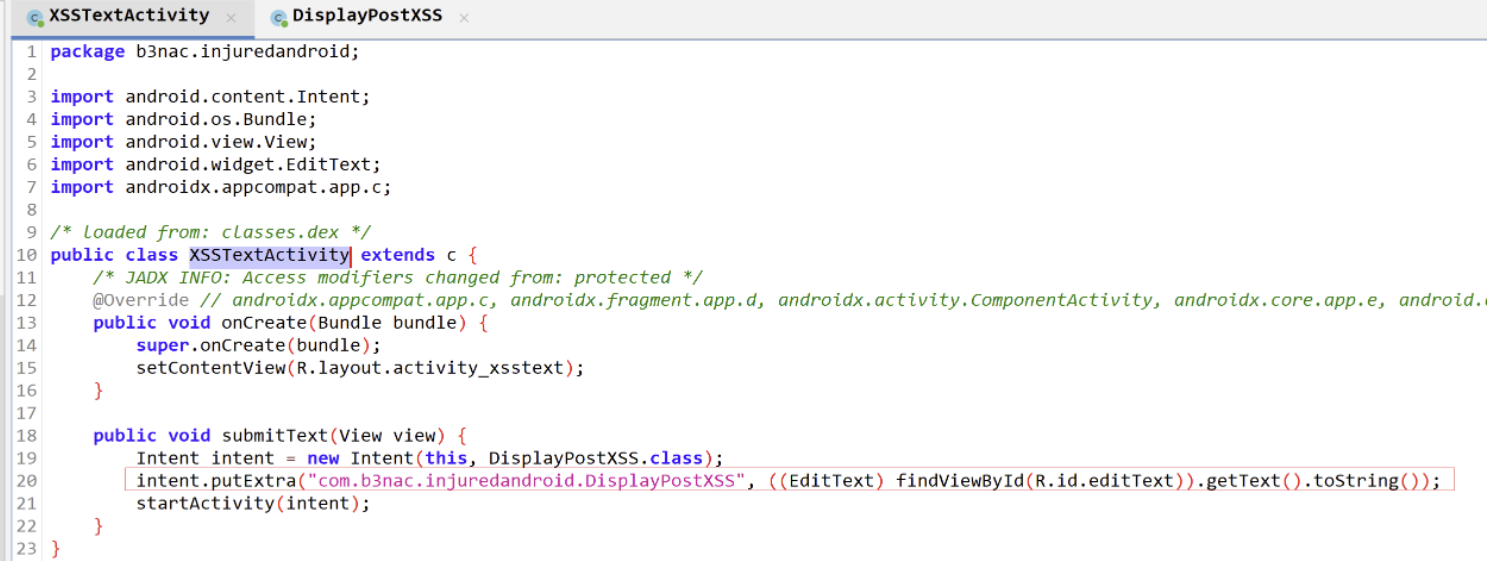
搜索找到XSSTextActivity: 发现提交之后会把输入传到DisplayPostXss
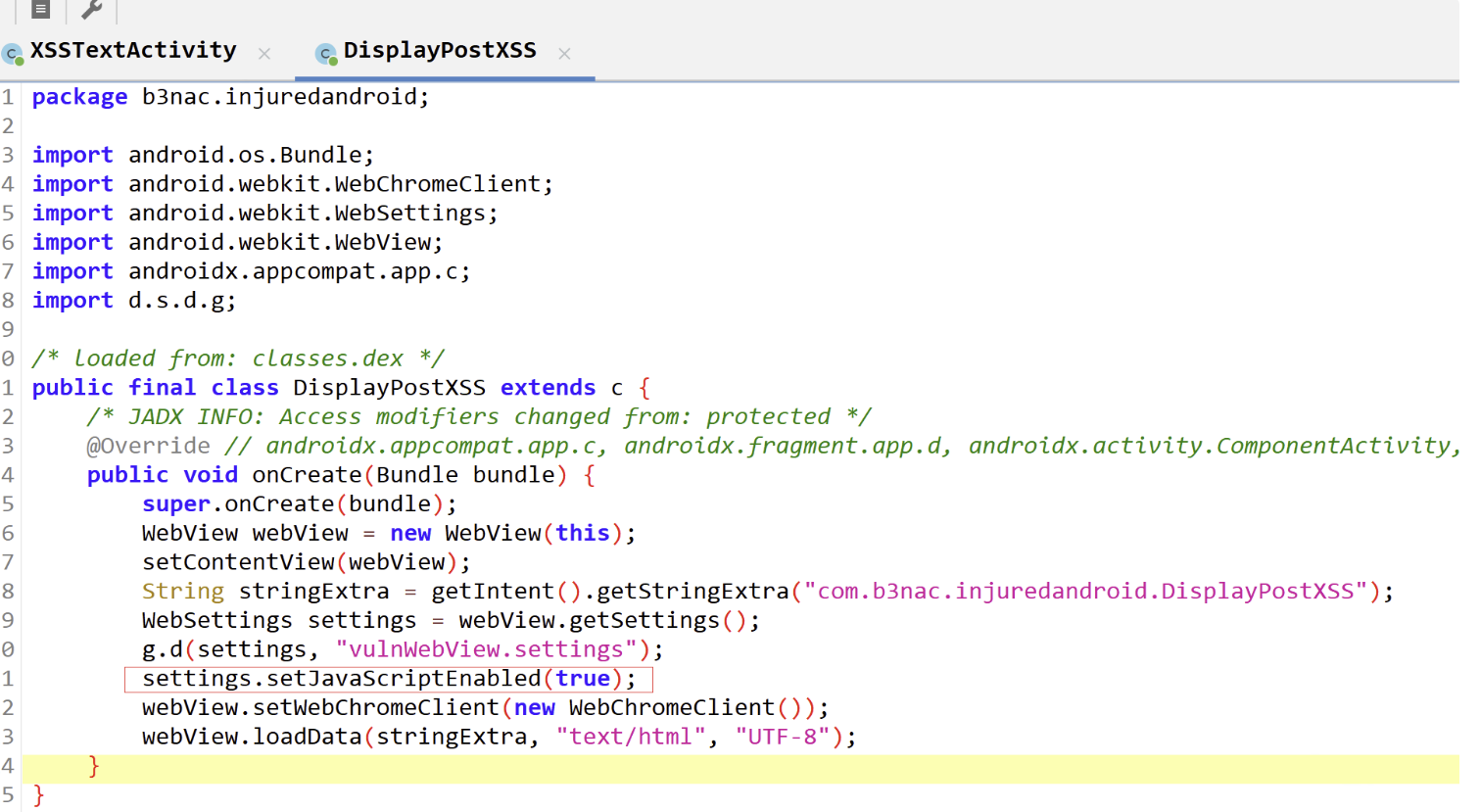
DisplayPostXss.class:发现可以执行js且没有什么限制,直接输入
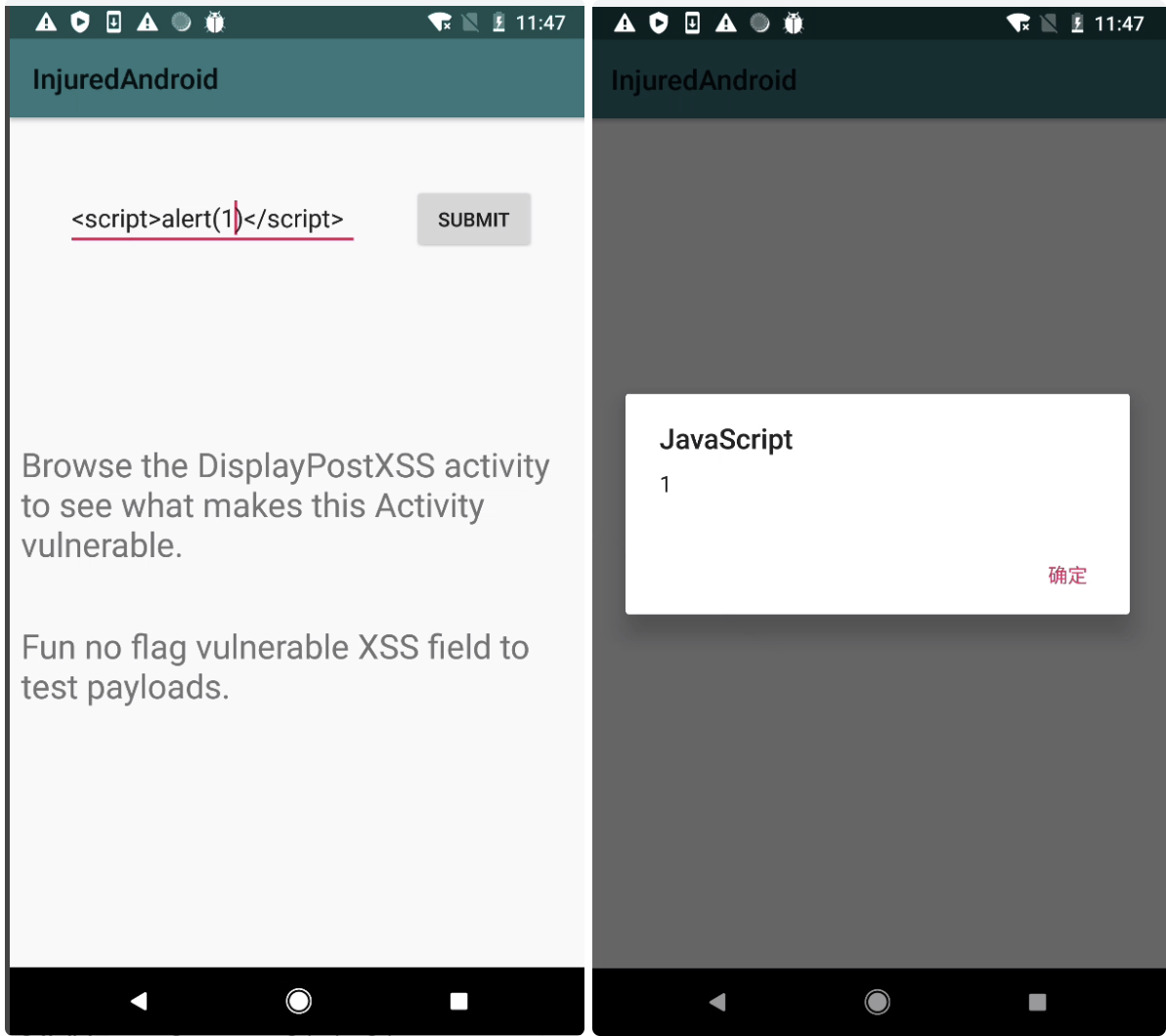
1 <script>alert(1)</script>
就可以触发xss
settings.setJavaScriptEnabled(true);
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 public final class DisplayPostXSS extends c { /* JADX INFO: Access modifiers changed from: protected */ @Override // androidx.appcompat.app.c, androidx.fragment.app.d, androidx.activity.ComponentActivity, androidx.core.app.e, android.app.Activity public void onCreate(Bundle bundle) { super.onCreate(bundle); WebView webView = new WebView(this); setContentView(webView); String stringExtra = getIntent().getStringExtra("com.b3nac.injuredandroid.DisplayPostXSS"); WebSettings settings = webView.getSettings(); g.d(settings, "vulnWebView.settings"); settings.setJavaScriptEnabled(true); webView.setWebChromeClient(new WebChromeClient()); webView.loadData(stringExtra, "text/html", "UTF-8"); } }
payload:
1 <script>alert(1)</script>
完成!
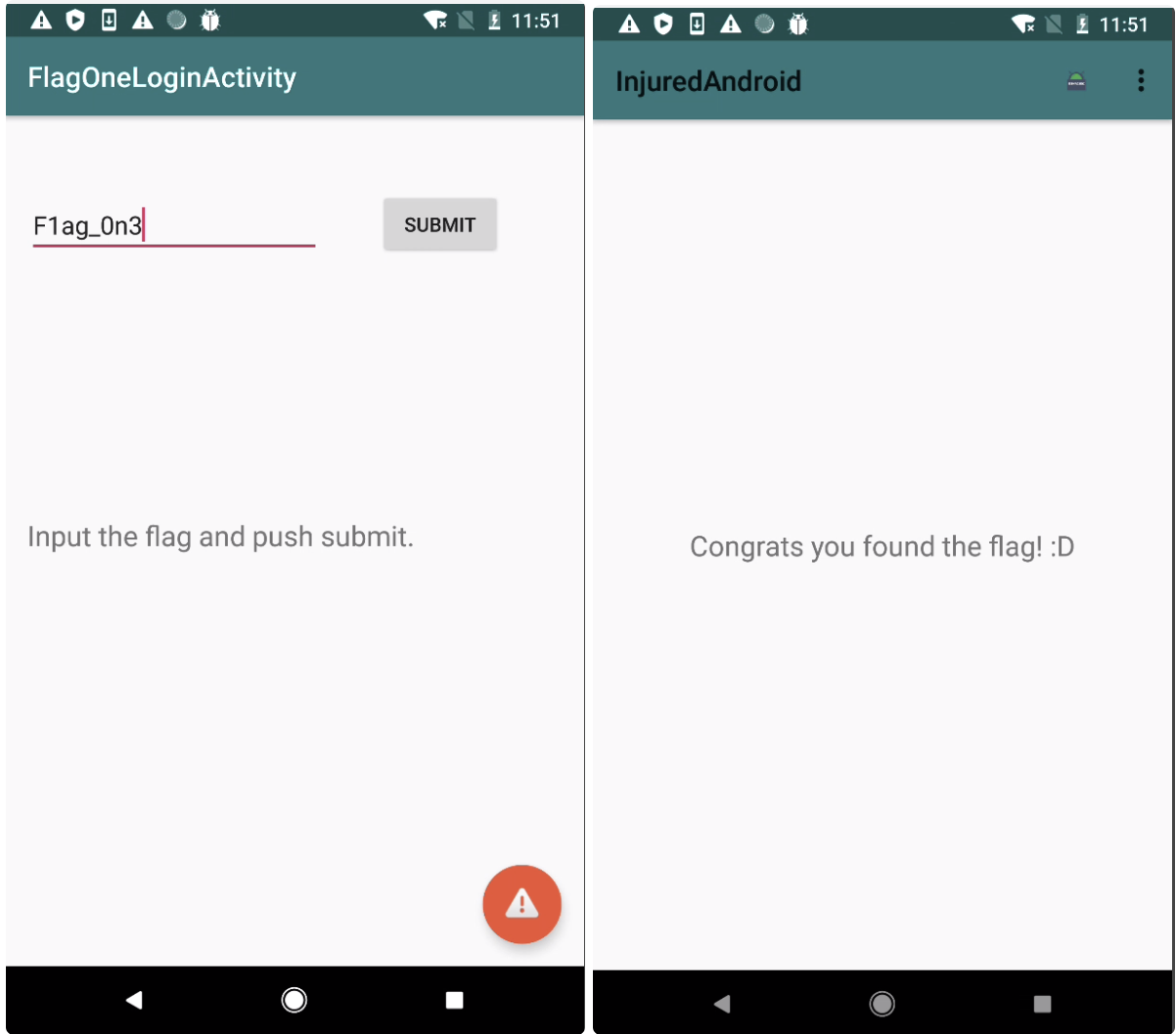
Challenge 1 FLAG ONE-LOGIN 根据提示:还是直接看代码
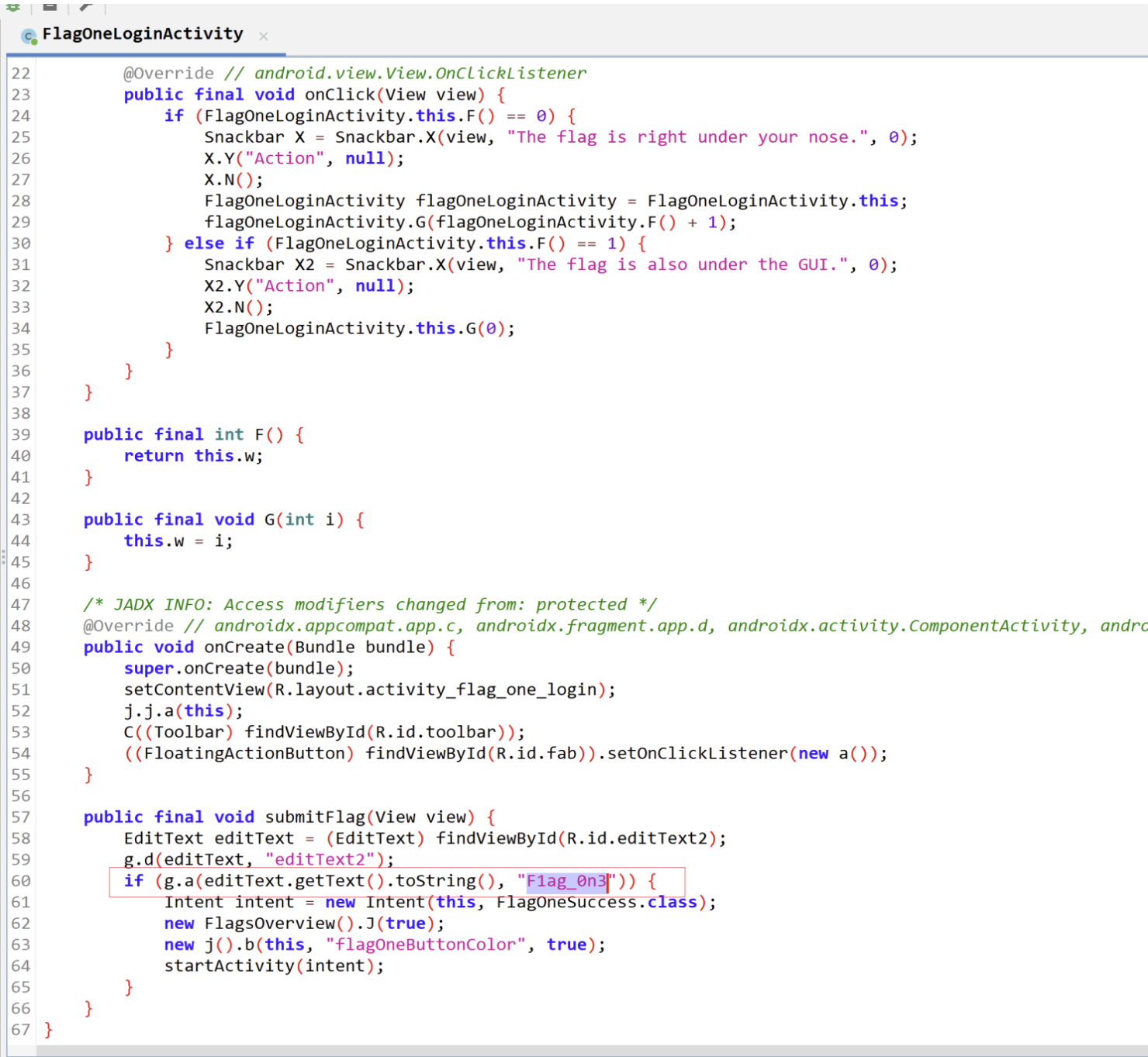
FlagOneLoginActivity:
获得flag:F1ag_0n3 尝试下
congrats you found the flag恭喜你找到了flag
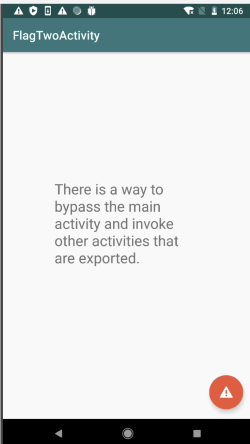
Challenge 2 FLAG TWO-EXPORTED ACTIVITY
没有按钮
根据标题导出的活动,猜测应该启动导出的活动
根据提示Exported Activities can be accessed with adb or Drozer,可以使用adb或drozer访问导出的活动
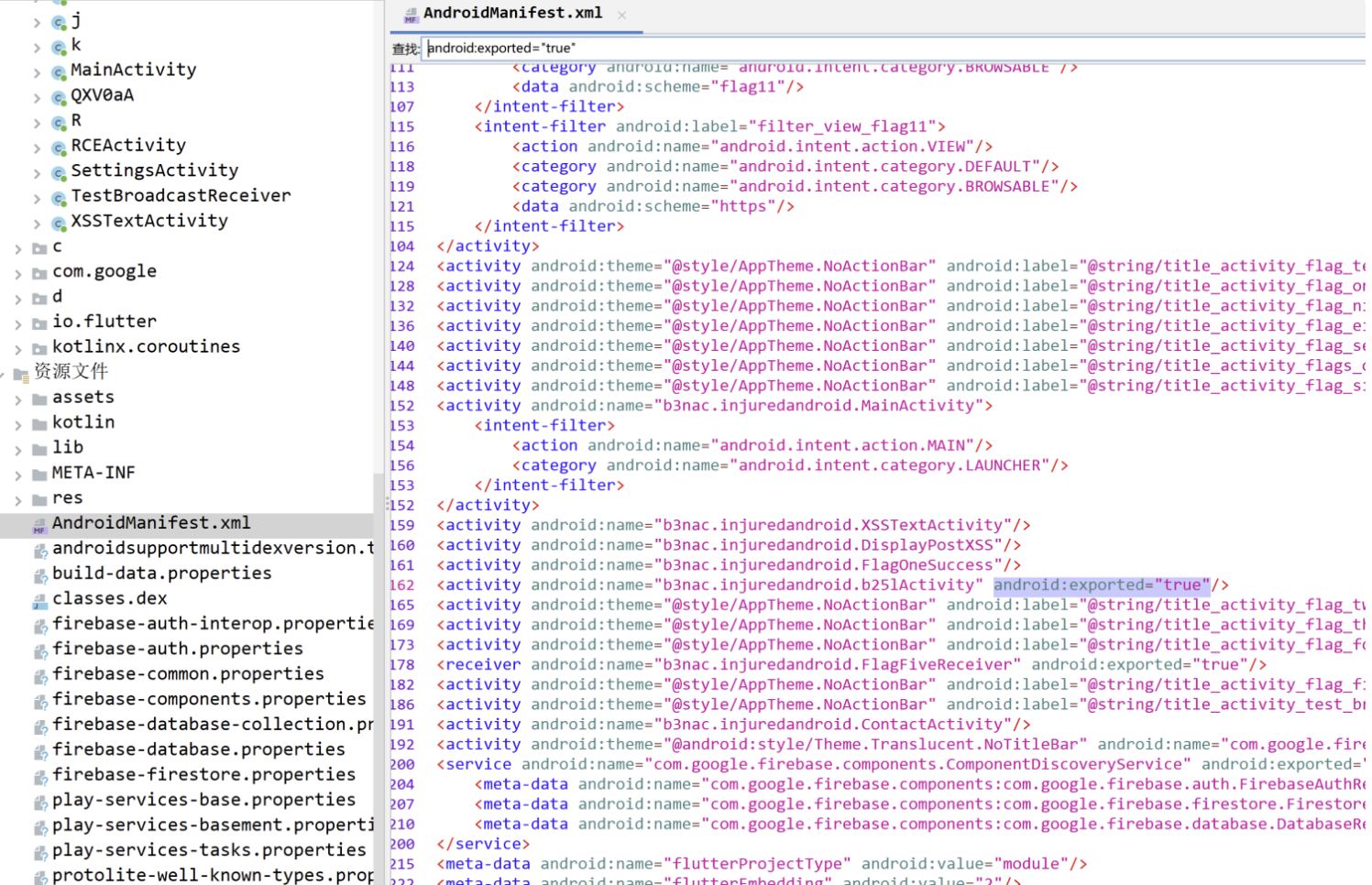
先打开AndroidManifest.xml
手动搜索导出的活动,android:exported=”true”,然后把导出的活动记录下来,手动搜索比较麻烦如果使用drozer可以用下面的命令,run app.activity.info -a ,就可以直接列出来导出的组件,启动activity,run app.activity.start –component <com.mwr.example.sieve> <com.mwr.example.sieve.MainLoginActivity>
b3nac.injuredandroid.FlagEighteenActivity
b3nac.injuredandroid.ExportedProtectedIntent
b3nac.injuredandroid.QXV0aA
b3nac.injuredandroid.b25lActivity
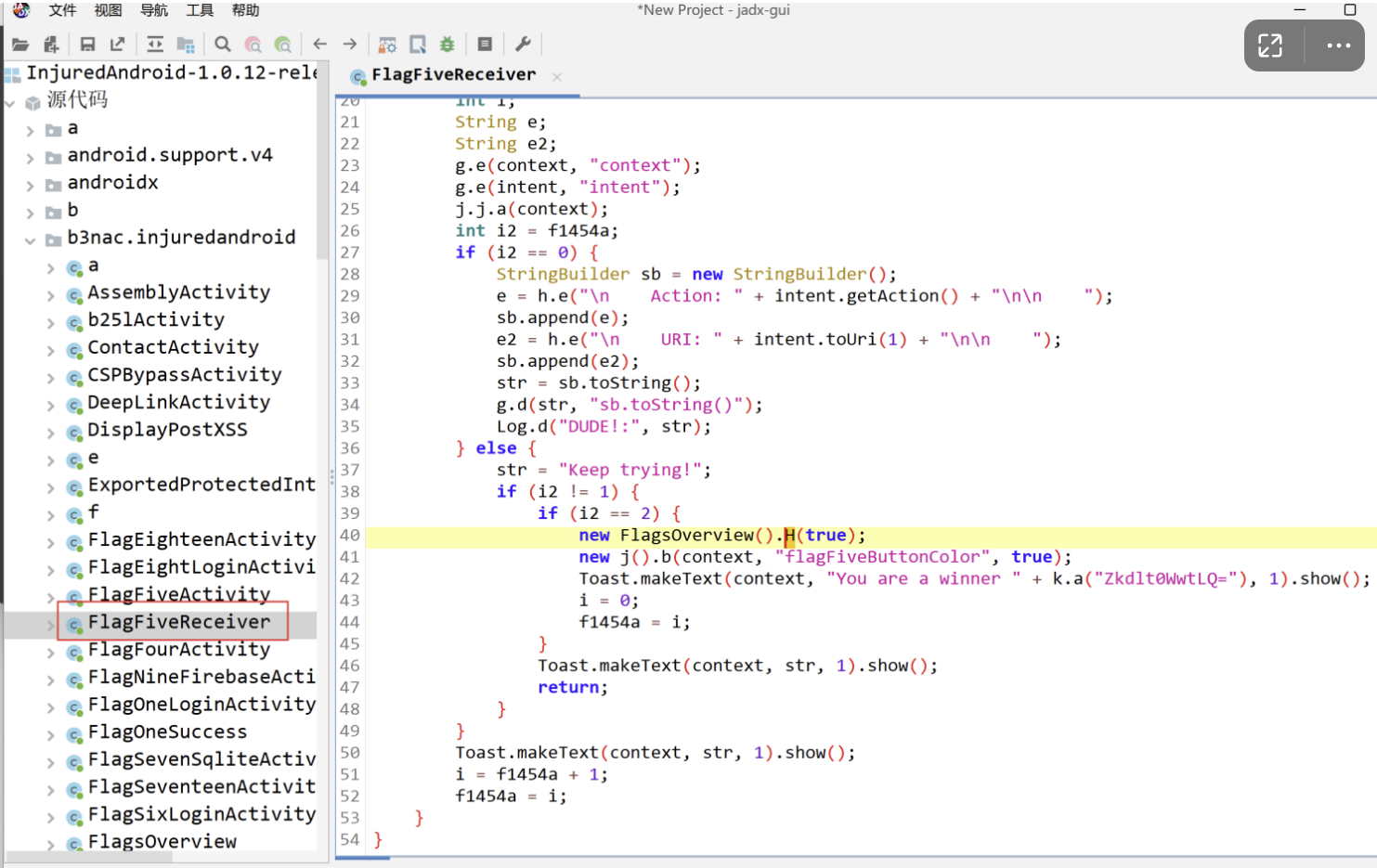
b3nac.injuredandroid.FlagFiveReceiver
b3nac.injuredandroid.TestBroadcastReceiver
com.google.firebase.auth.internal.FederatedSignInActivity
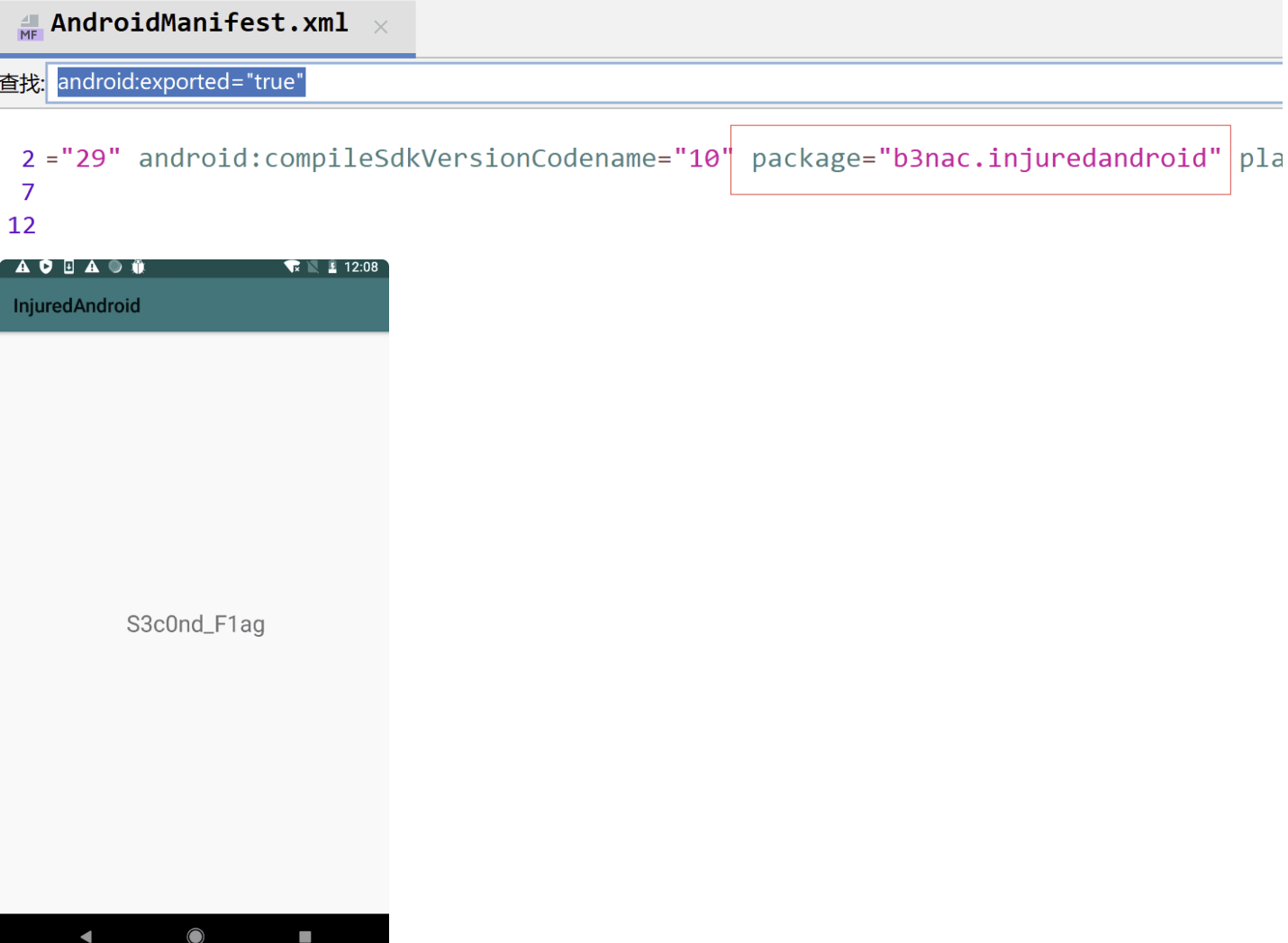
猜测是b25lActivity这个,使用adb打开试下
adb shell am start -n b3nac.injuredandroid/b3nac.injuredandroid.b25lActivity
包名可以在AndroidMaifest.xml找
完成!
Challenge 3 FLAG THREE-RESOURCES 打开,提示要看资源文件
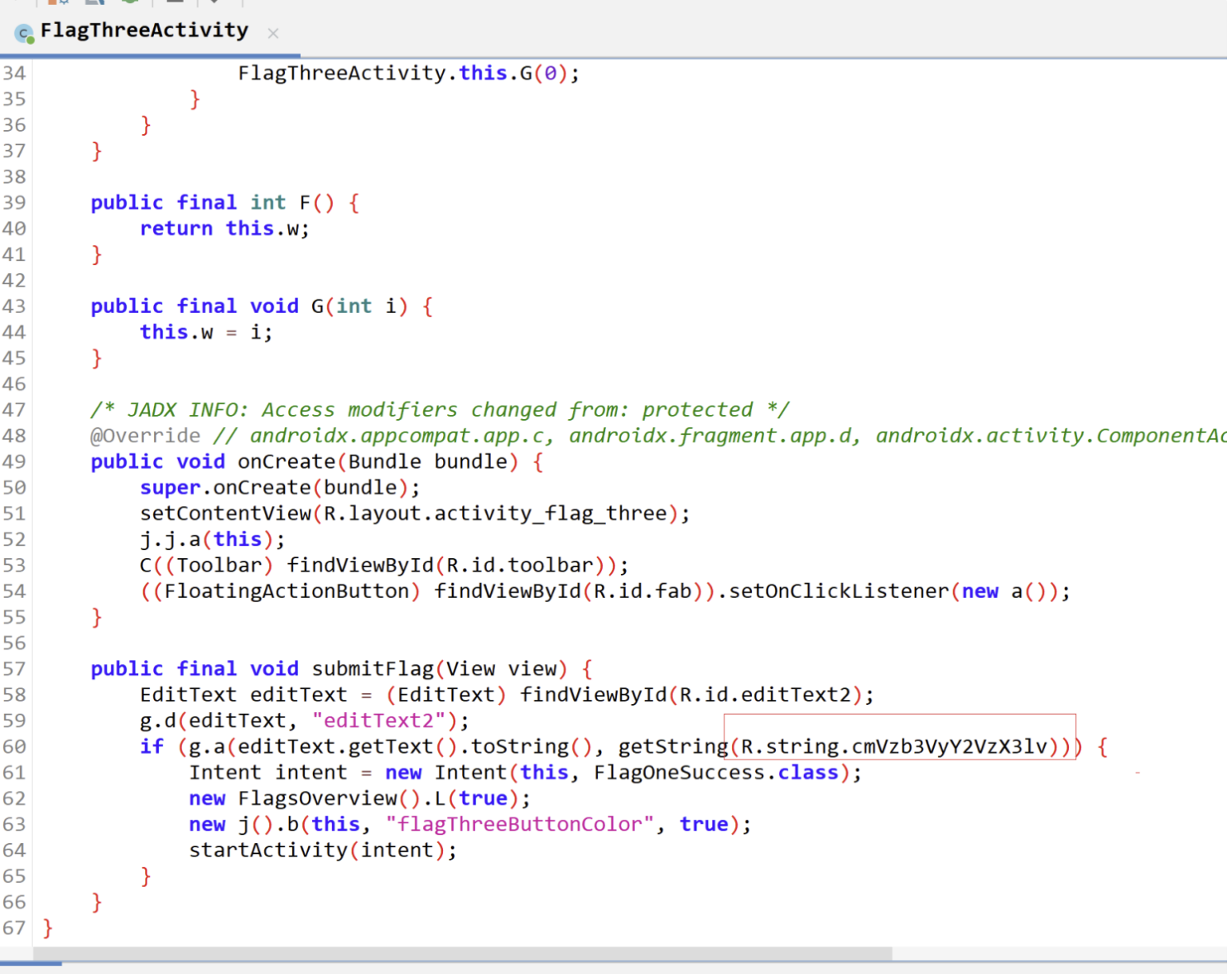
看代码FlagThreeActivity:
搜索cmVzb3VyY2VzX3lv
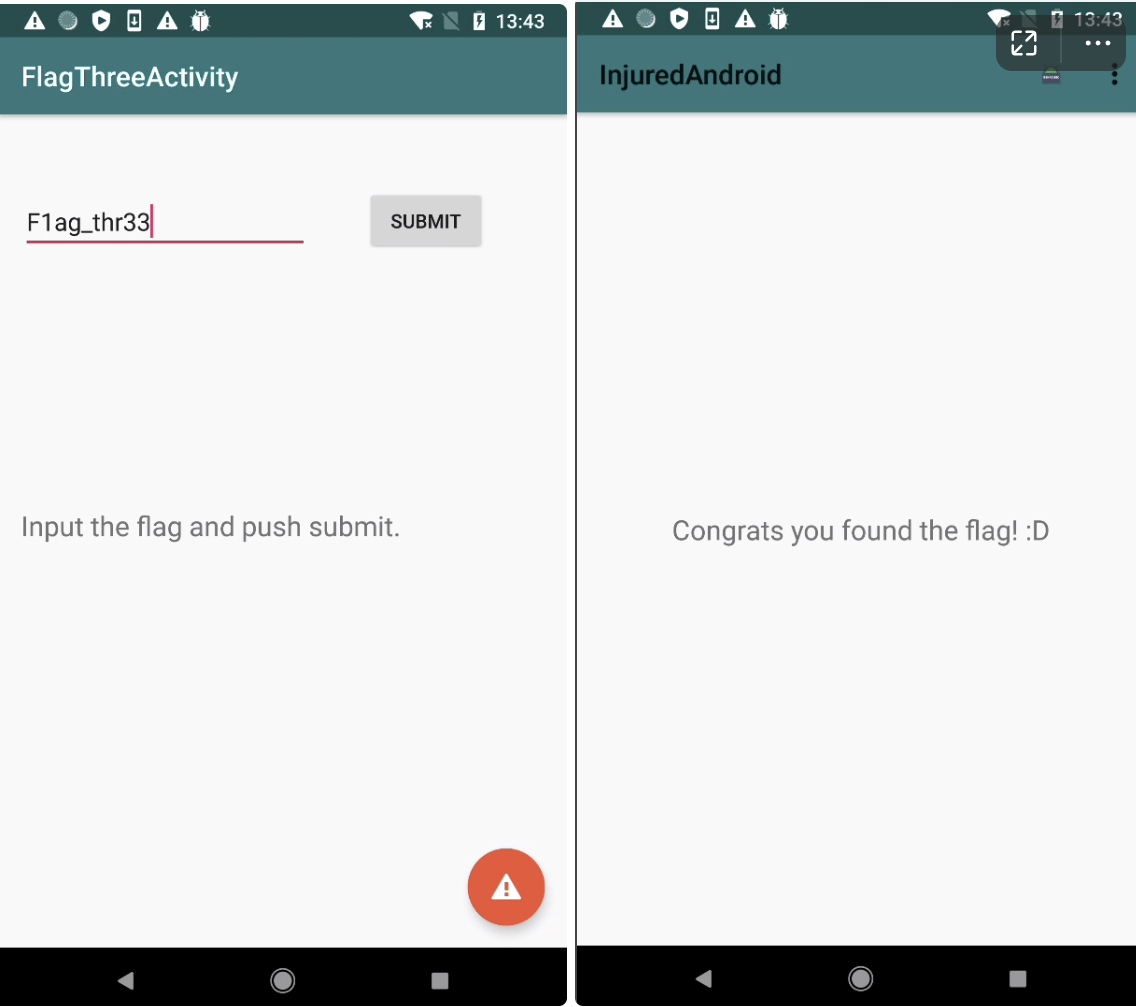
尝试一下F1ag_thr33
完成了!
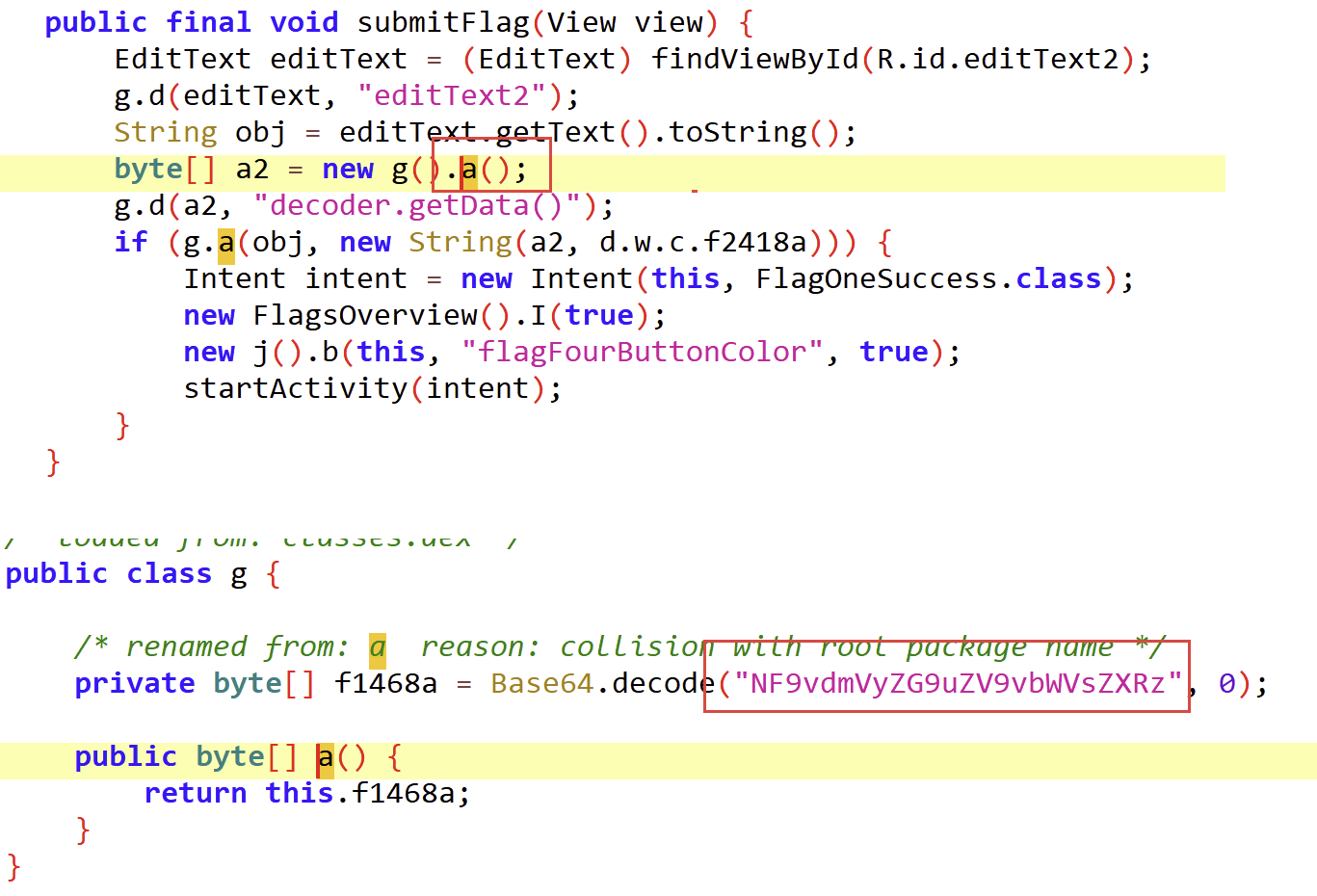
Challenge 4 FLAG FOUR-LOGIN 2 还是先看代码
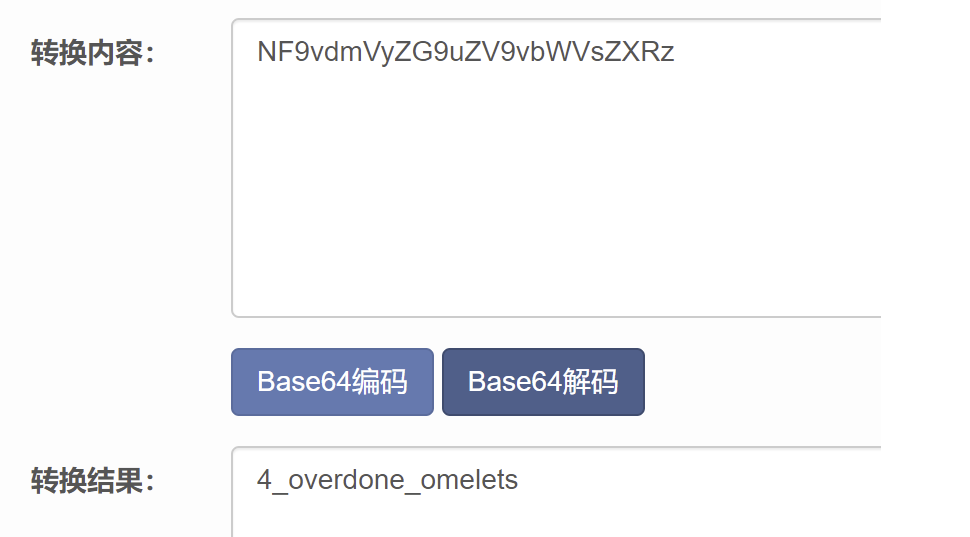
有一个base64的字符串,解析一下 NF9vdmVyZG9uZV9vbWVsZXRz
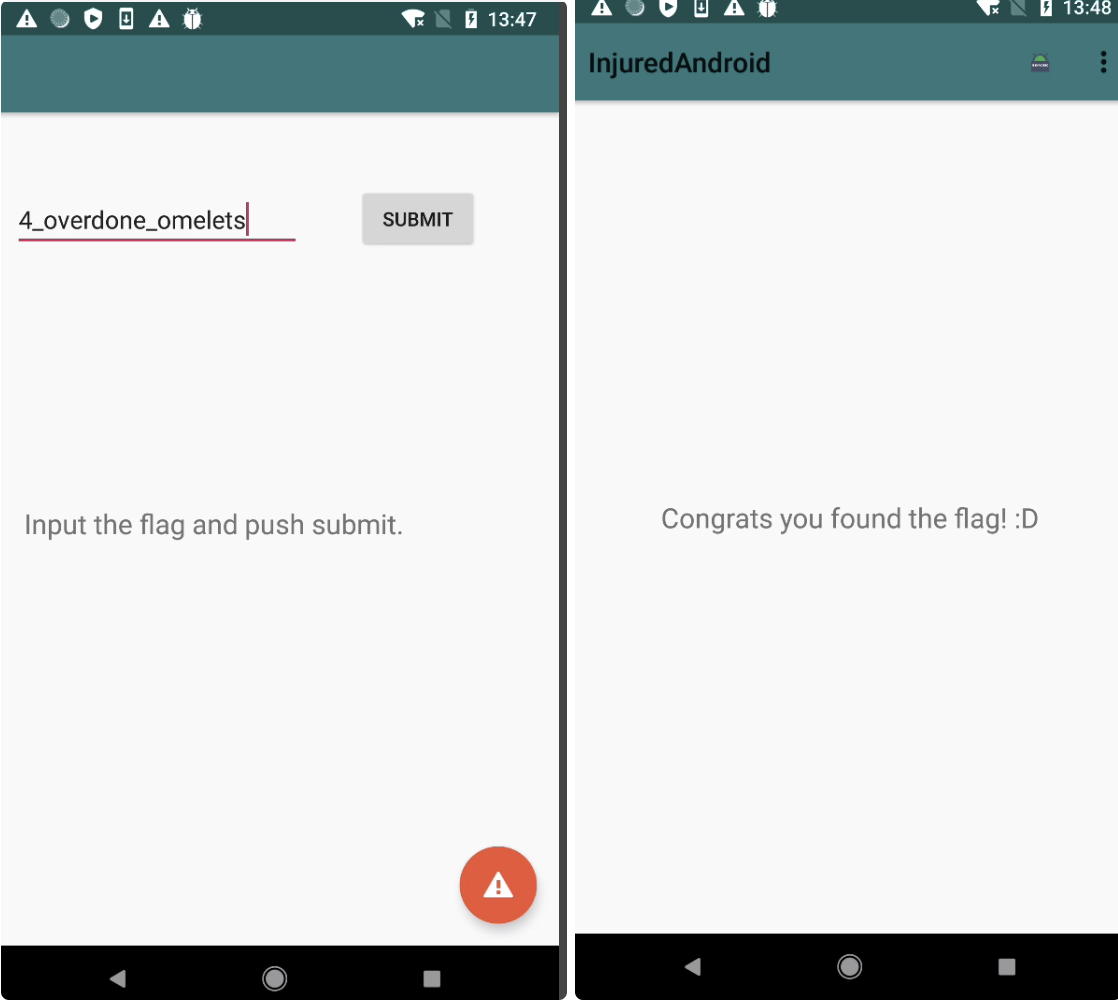
尝试一下,4_overdone_omelets
完成了!
Challenge 5 FLAG FIVE-EXPORTED BROADCAST RECEIVER 提示
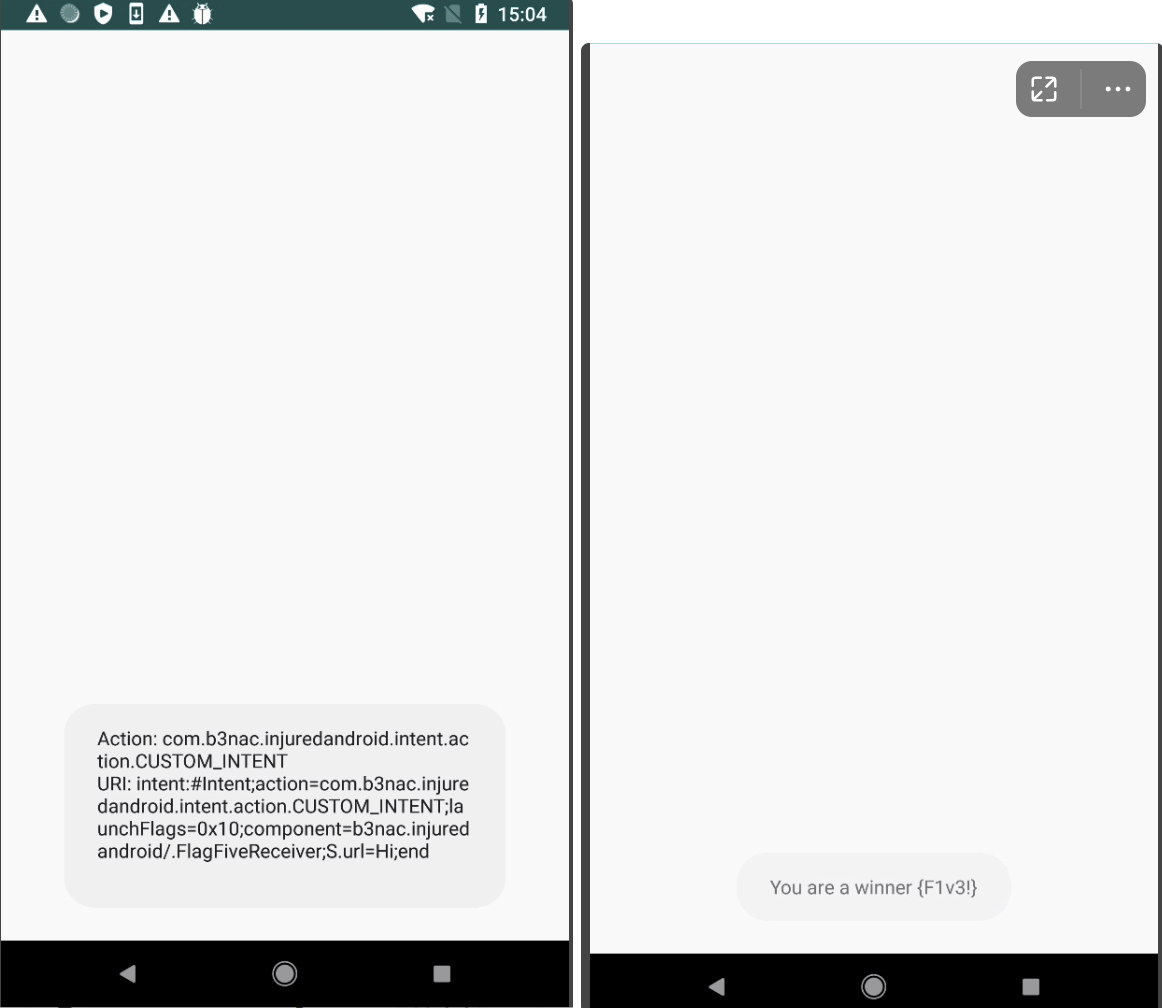
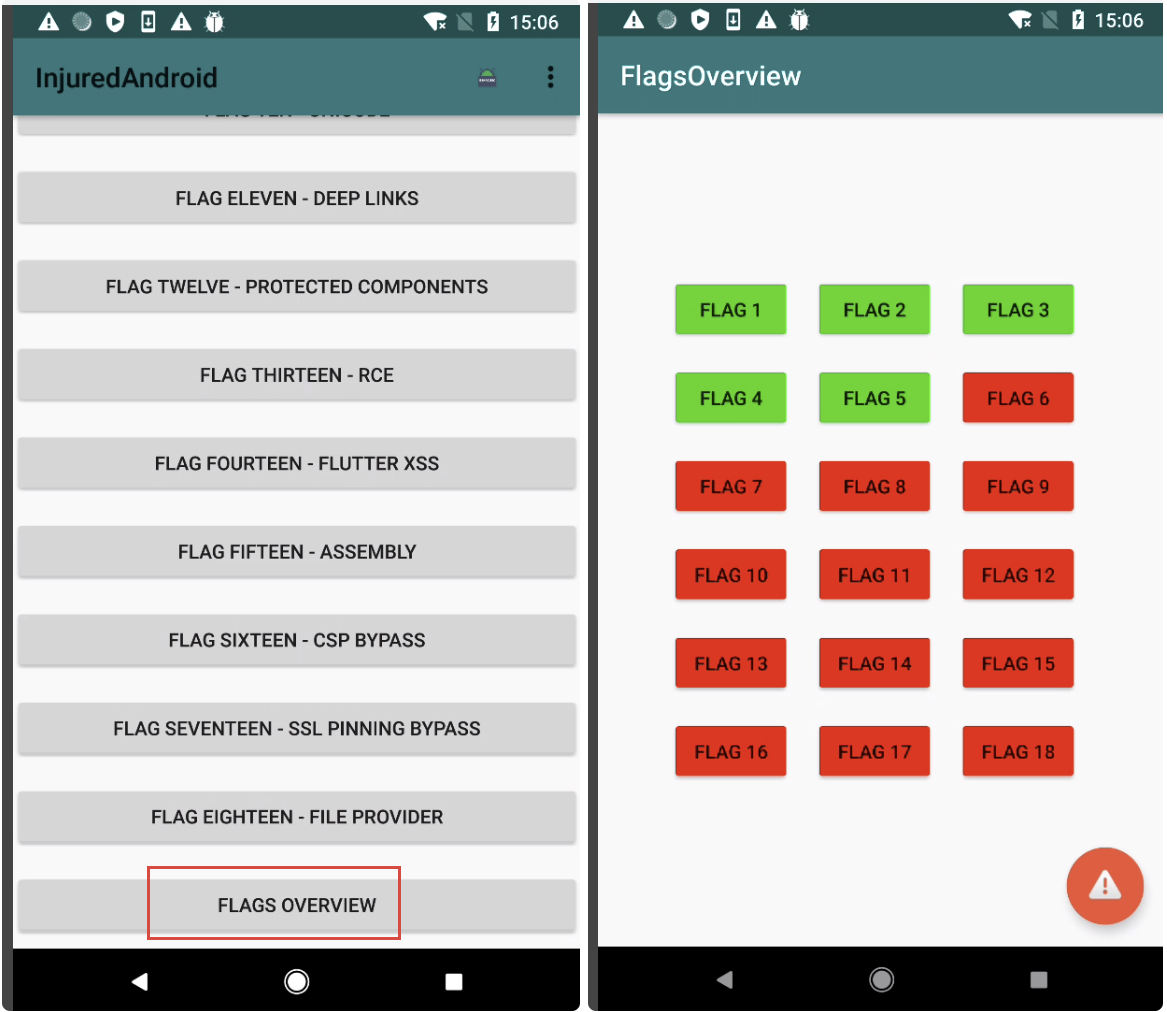
根据提示应该需要打开fivereceiver,然后不知道出了什么问题 点击five三次之后就出来flag,看flags overview,还通过了
看下静态分析下是否可以解密出来,网上搜索有的用frida动态hook出来的,等下也试试
静态分析:
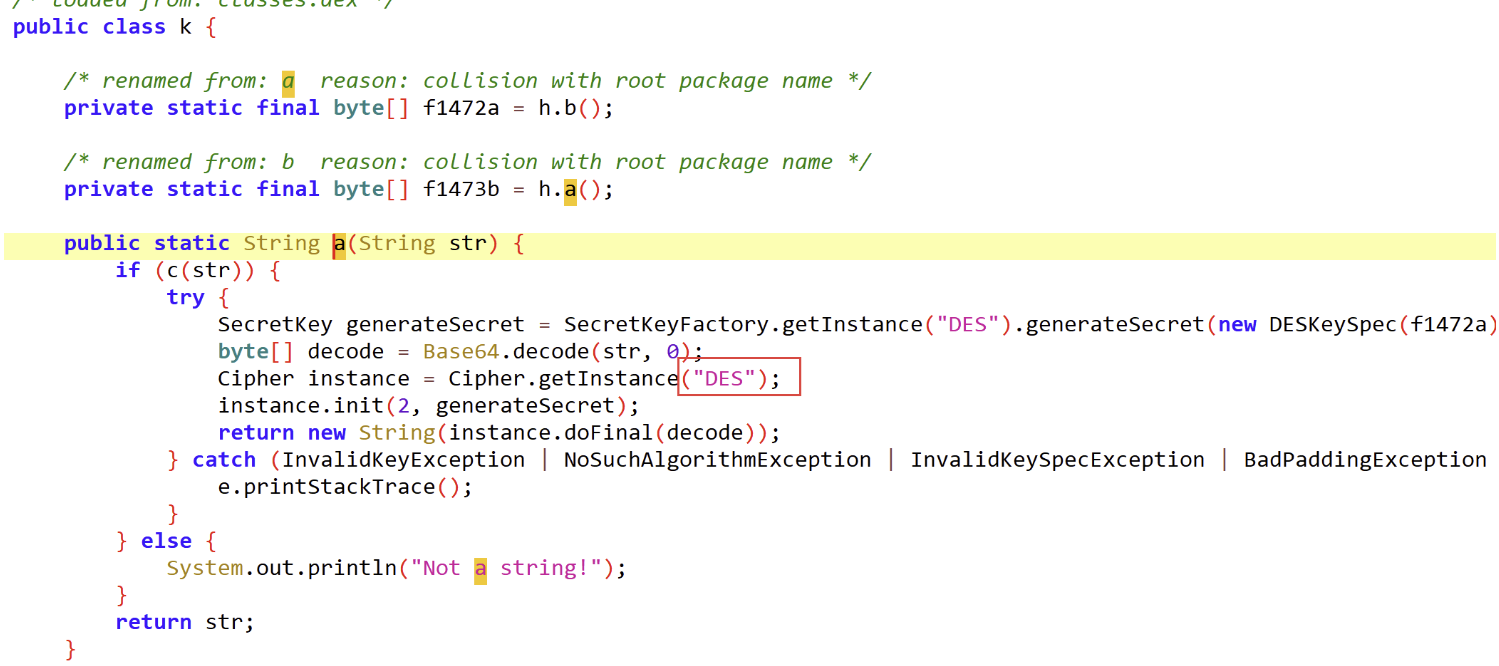
看样子应该要解密出来Zkdlt0WwtLQ=,看下a方法里有什么
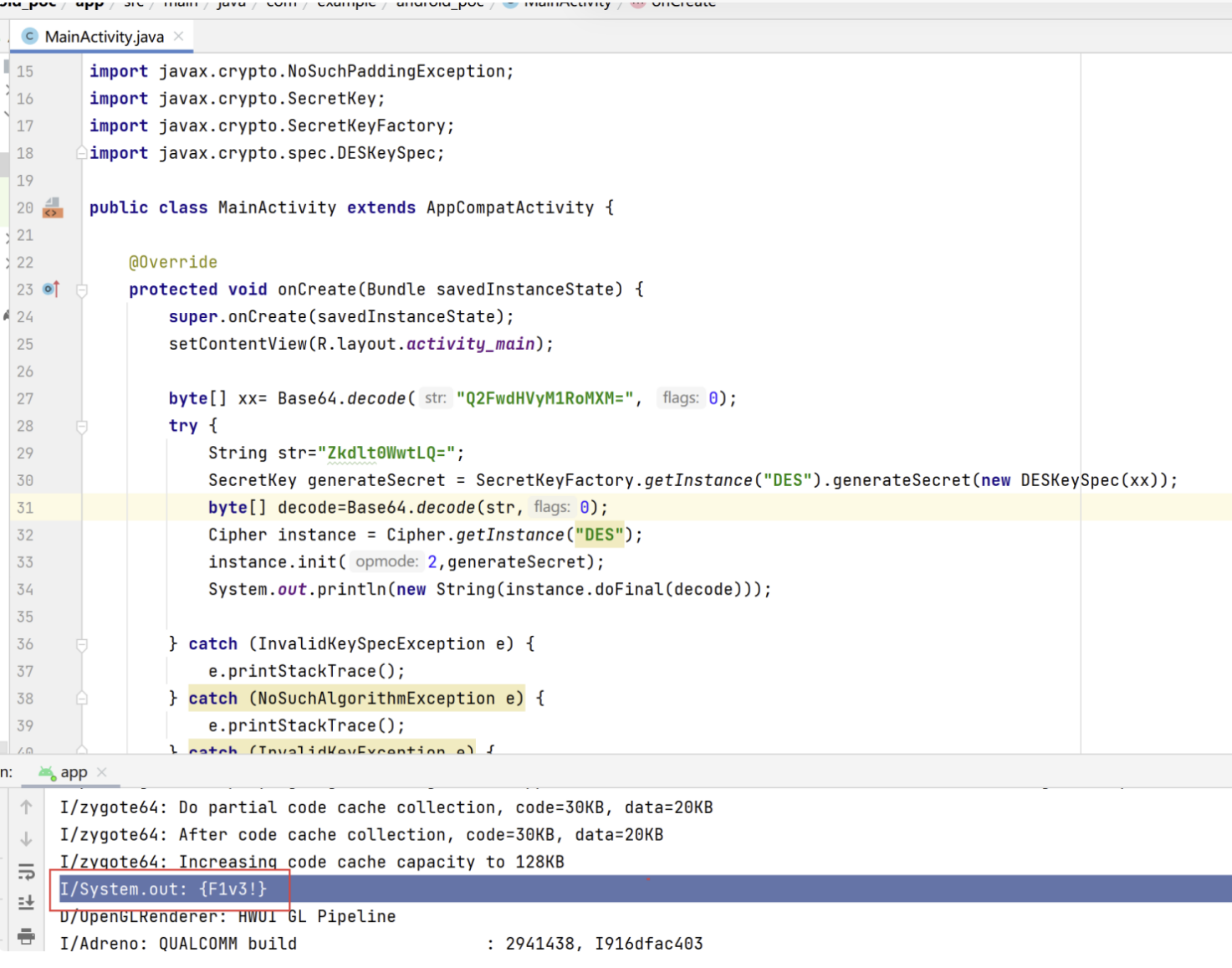
des解密,直接复制出来可以获得flag
code:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 package com.example.android_poc; import androidx.appcompat.app.AppCompatActivity; import android.os.Bundle; import android.util.Base64; import java.security.InvalidKeyException; import java.security.NoSuchAlgorithmException; import java.security.spec.InvalidKeySpecException; import javax.crypto.BadPaddingException; import javax.crypto.Cipher; import javax.crypto.IllegalBlockSizeException; import javax.crypto.NoSuchPaddingException; import javax.crypto.SecretKey; import javax.crypto.SecretKeyFactory; import javax.crypto.spec.DESKeySpec; public class MainActivity extends AppCompatActivity { @Override protected void onCreate(Bundle savedInstanceState) { super.onCreate(savedInstanceState); setContentView(R.layout.activity_main); //密钥 byte[] xx= Base64.decode("Q2FwdHVyM1RoMXM=", 0); try { //字符串 String str="Zkdlt0WwtLQ="; SecretKey generateSecret = SecretKeyFactory.getInstance("DES").generateSecret(new DESKeySpec(xx)); byte[] decode=Base64.decode(str,0); Cipher instance = Cipher.getInstance("DES"); instance.init(2,generateSecret); System.out.println(new String(instance.doFinal(decode))); } catch (InvalidKeySpecException e) { e.printStackTrace(); } catch (NoSuchAlgorithmException e) { e.printStackTrace(); } catch (InvalidKeyException e) { e.printStackTrace(); } catch (NoSuchPaddingException e) { e.printStackTrace(); } catch (IllegalBlockSizeException e) { e.printStackTrace(); } catch (BadPaddingException e) { e.printStackTrace(); } } }
frida:
由于我现在的测试机是pixel xl 安装最新版本的frida 好像带不动,所以就卸载了 安装了低版本的
安装frida:
1 2 3 4 activate base pip install frida-tools==5.3.0 pip install frida==12.8.0 pip install objection==1.8.4
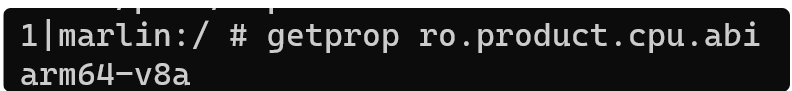
查看手机cpu型号:
1 2 3 4 5 6 adb shell su getprop ro.product.cpu.abi --- 1|marlin:/ # getprop ro.product.cpu.abi arm64-v8a
下载对应版本的frida-server
解压后 修改名fs1280arm64
1 2 3 4 5 6 λ adb push fs1280arm64 /data/local/tmp λ adb shell marlin:/ $ su marlin:/ # cd /data/local/tmp marlin:/data/local/tmp # chmod 755 fs1280arm64 marlin:/data/local/tmp # ./fs1280arm64
five.js代码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 function intercept(){ if(Java.available){ Java.perform(function(){ const myreceiver = Java.use('b3nac.injuredandroid.FlagFiveReceiver'); var Activity = Java.use("android.app.Activity"); var Intent=Java.use("android.content.Intent"); myreceiver.onReceive.overload('android.content.Context','android.content.Intent').implementation = function(context,intent){ console.log("[+] received a broadcast"); var myintent = Java.cast(intent,Intent); console.log("[+] intent is "+myintent.toUri(0)); var myaction = myintent.getAction(); var mycomponent = myintent.getComponent(); var myextras = myintent.getExtras(); console.log('[+] action is '+myaction.toString()); console.log('[+] component is '+mycomponent.toString()); if (myextras){ console.log('[+] extras is '+myextras.toString()); } this.onReceive(context,intent); } console.log("[+] FlagFiveReceiver.onReceiver hooked"); }) } } intercept();
运行
frida -f b3nac.injuredandroid -l five.js
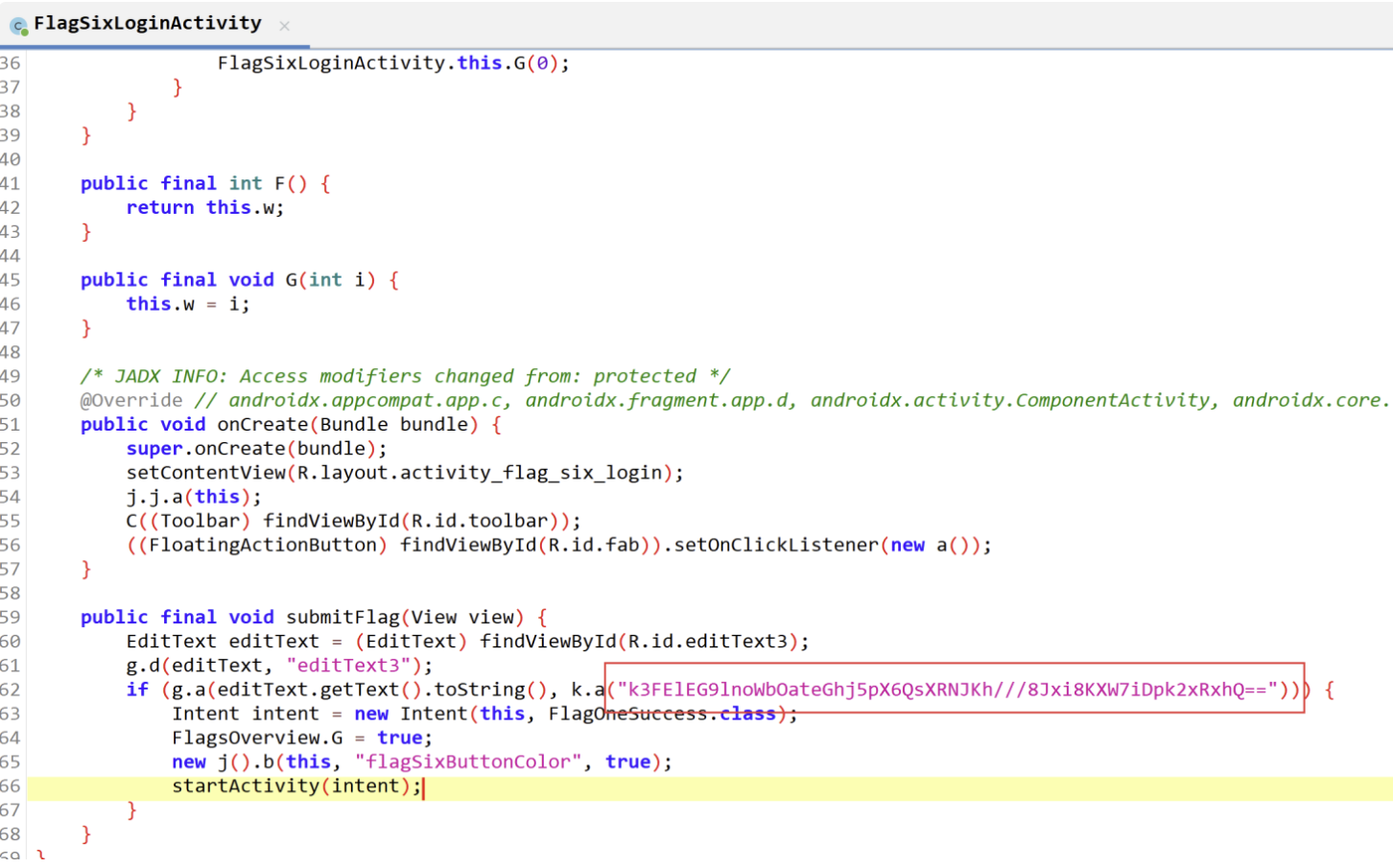
Challenge 6 FLAG SIX-LOGIN 3 打开代码
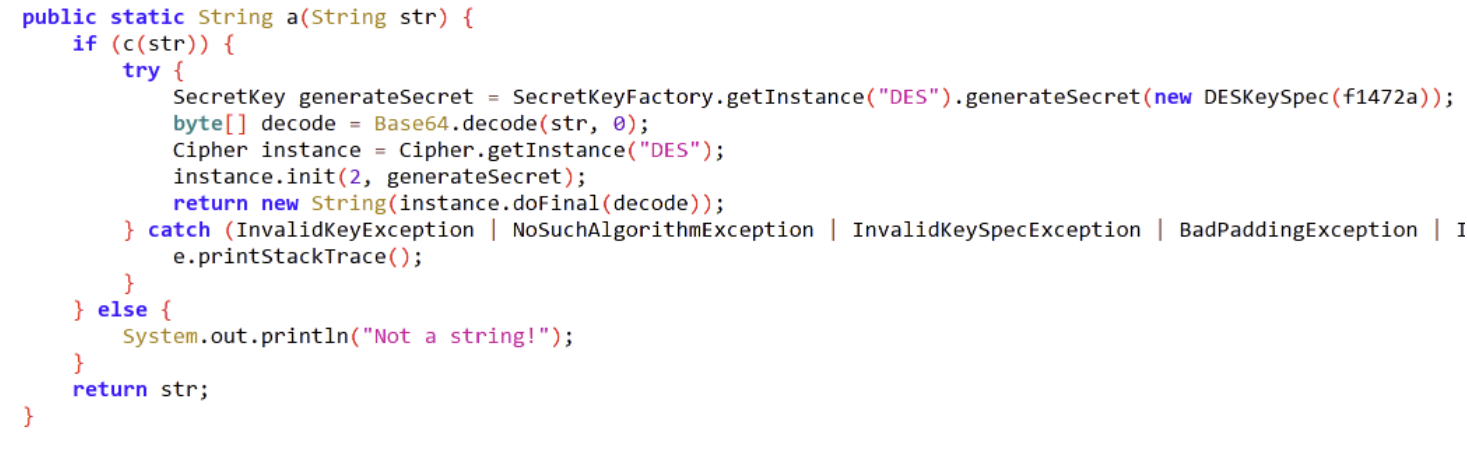
看来又是加密,跟5一样,把加密字符串修改下就好了
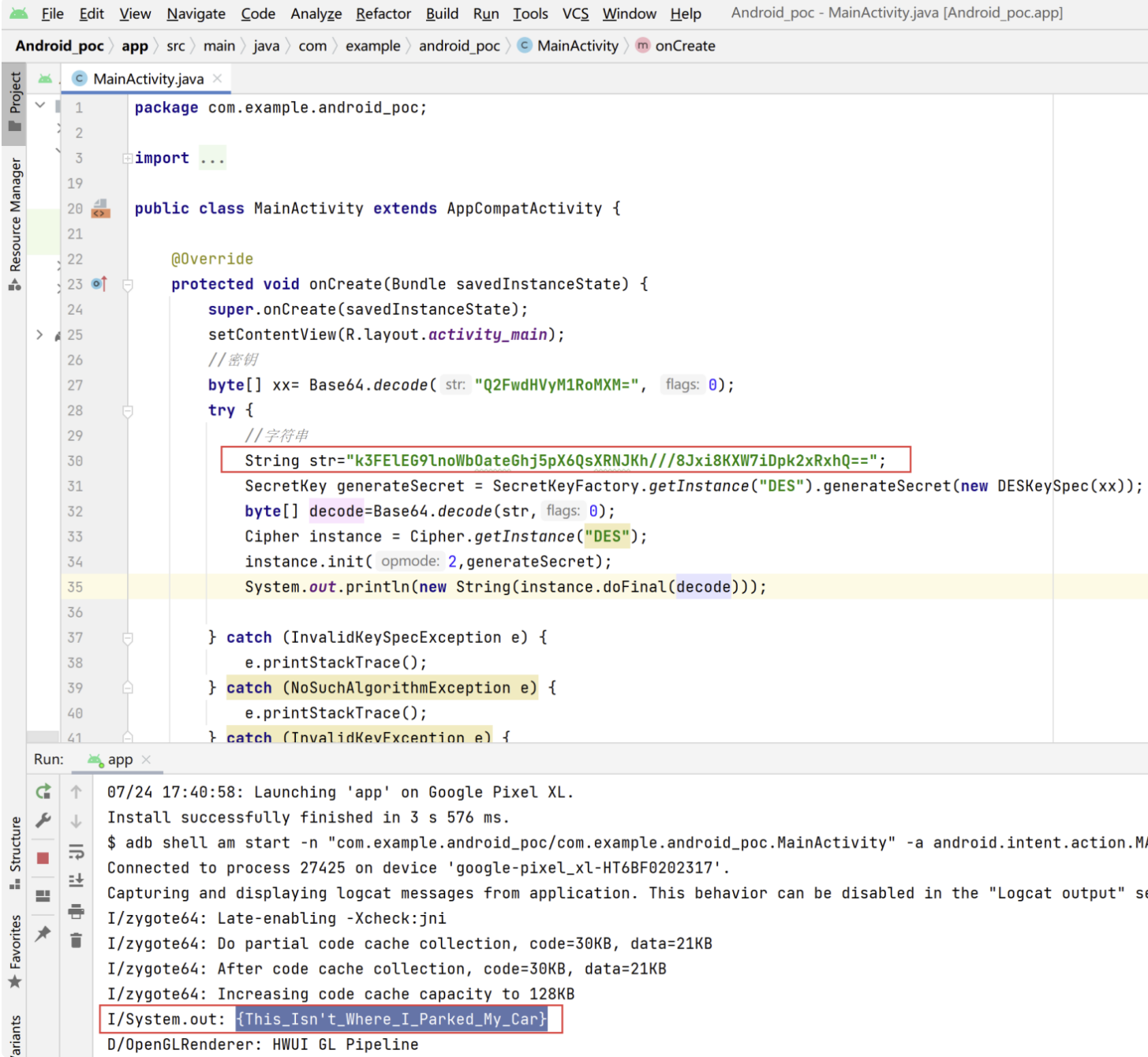
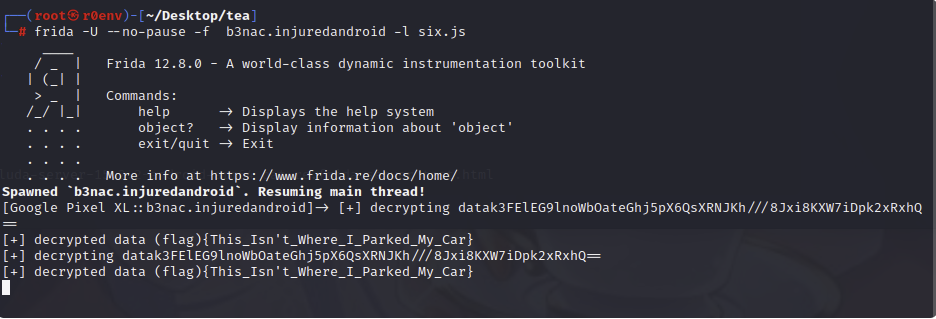
k3FElEG9lnoWbOateGhj5pX6QsXRNJKh///8Jxi8KXW7iDpk2xRxhQ==
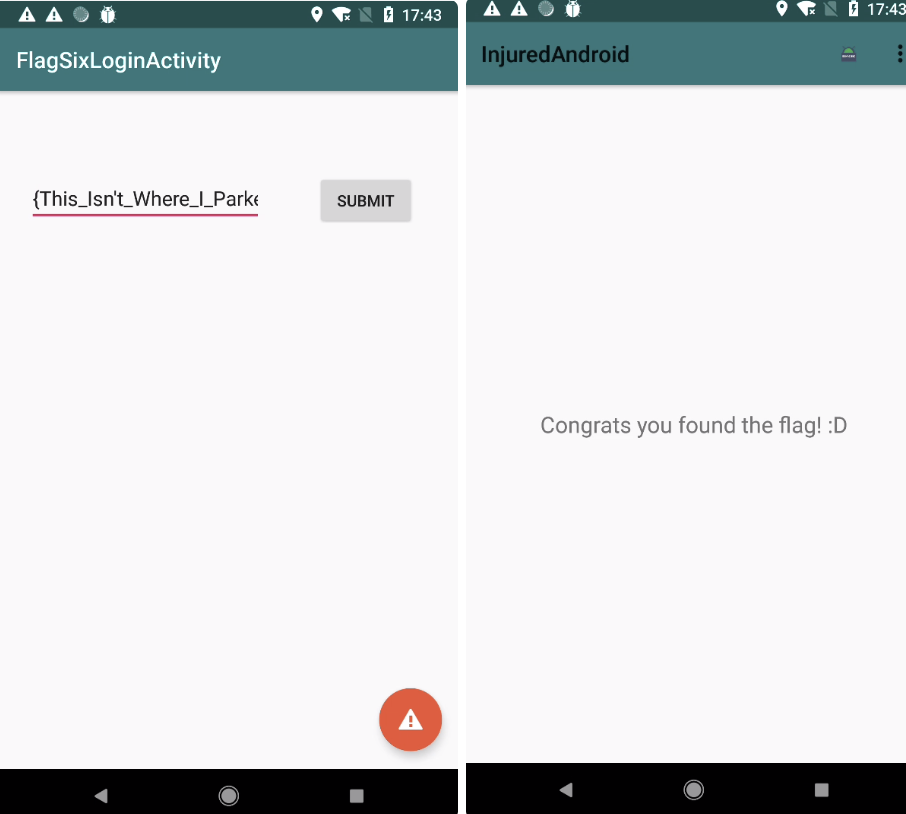
flag:{This_Isn’t_Where_I_Parked_My_Car}
frida:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 function intercept(){ Java.perform(function(){ const mydecrypt = Java.use('b3nac.injuredandroid.k'); mydecrypt.a.overload('java.lang.String').implementation = function(data){ console.log('[+] decrypting data'+data) var flag=this.a(data); console.log('[+] decrypted data (flag)'+flag); return flag; } }) } intercept();
frida -U –no-pause -f b3nac.injuredandroid -l six.js
完成
第七关,没尝试成功,在之后都是需要感觉都是联网获取,大多已经没提供服务了
Author:
tea9
Permalink:
http://tea9.xyz/post/505929609.html
License:
Copyright (c) 2017-2023 CC-BY-NC-4.0 LICENSE
Slogan:
Do you believe in DESTINY ?